Security researchers have uncovered a critical vulnerability in multiple D-Link NAS (Network Attached Storage) devices that could allow attackers to execute arbitrary commands and gain unauthorized access. The vulnerabilities, tracked as CVE-2024-3273, are currently under active exploitation, putting thousands of devices at risk.
The affected D-Link NAS models include DNS-340L, DNS-320L, DNS-327L, DNS-325, and others. The vulnerabilities reside within the nas_sharing.cgi URI, which is vulnerable due to two main issues: a backdoor facilitated by hardcoded credentials, and a command injection vulnerability through the system parameter.
Hardcoded Credentials Backdoor
The vulnerability exposes hardcoded credentials, allowing unauthorized access without proper authentication. The request includes parameters for a username (user=messagebus) and an empty password field (passwd=), indicating a backdoor that bypasses authentication mechanisms.
Command Injection Vulnerability
The system parameter within the request carries a base64 encoded value that, when decoded, appears to be a command. This command injection vulnerability enables attackers to execute arbitrary commands on the affected D-Link NAS devices, potentially leading to unauthorized access to sensitive information, system configuration alteration, or denial of service conditions.
Craft Malicious HTTP Request: Prepare an HTTP GET request targeting the /cgi-bin/nas_sharing.cgi endpoint.
GET /cgi-bin/nas_sharing.cgi?user=messagebus&passwd=&cmd=15&system=<BASE64_ENCODED_COMMAND_TO_BE_EXECUTED>Active Exploitation
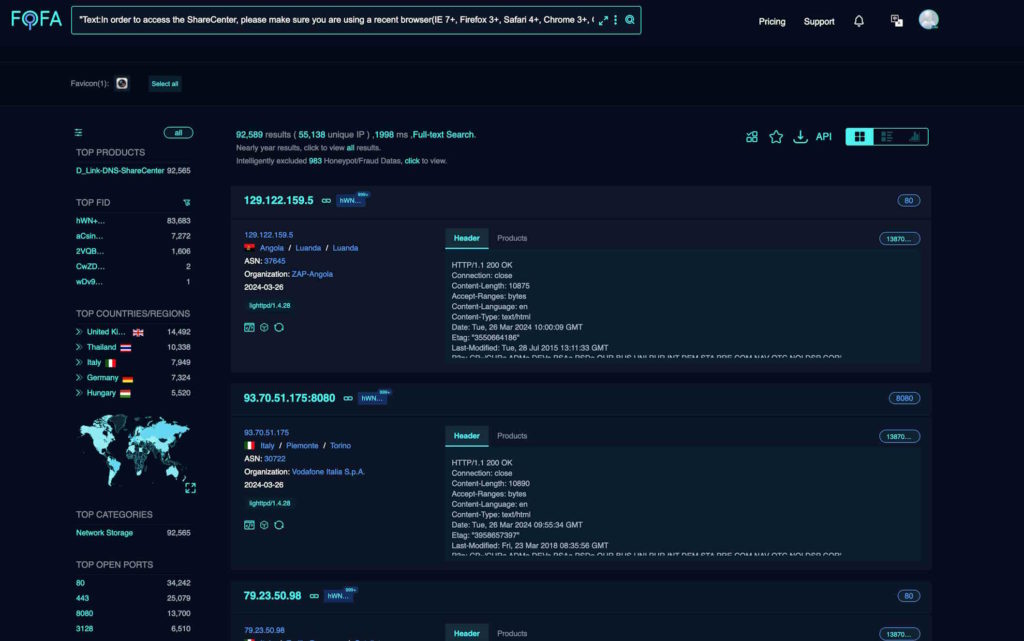
Security researchers have observed active exploitation attempts targeting this vulnerability, with over 92,000 devices connected to the internet potentially at risk. Successful exploitation could grant attackers control over the compromised devices, allowing them to steal data, modify system configurations, or disrupt operations.
Recommendations
D-Link has been notified of these vulnerabilities, and users are strongly advised to apply available patches and updates from the device manufacturer as soon as possible. Additionally, users should review their router’s UPnP configuration to ensure that their NAS devices are not exposed to potential attacks.