ServiceNow has patched three critical security vulnerabilities that could have allowed remote hackers to expose and access to sensitive data and execute malicious code on thousands of instances of its popular ITSM platform.
The Vulnerabilities
Security research team Assetnote disclosed three critical security flaws in ServiceNow’s platforms in May 2024. These vulnerabilities, now tracked as CVE-2024-4879, CVE-2024-5178, and CVE-2024-5217, affected multiple ServiceNow releases and posed serious risks to businesses worldwide.
CVE-2024-4879
Jelly Template Injection Vulnerability This flaw in ServiceNow UI Macros could allow an unauthenticated user to execute code remotely within the Now Platform. It’s like leaving your front door wide open for intruders.
CVE-2024-5178
Incomplete Input Validation in SecurelyAccess API.
This vulnerability could give administrative users unauthorized access to sensitive files on the web application server.
CVE-2024-5217
Incomplete Input Validation in GlideExpression Script. Similar to the first vulnerability, this flaw could enable unauthenticated users to execute code remotely.
The Scale of the Problem
To put things in perspective, search engine data from FOFA indicates over 129,000 exposed ServiceNow instances. That’s a lot of potentially vulnerable systems out there. While shodan shows only around 9000 ServiceNow instances.
FOFA Dork
app="servicenow-Products"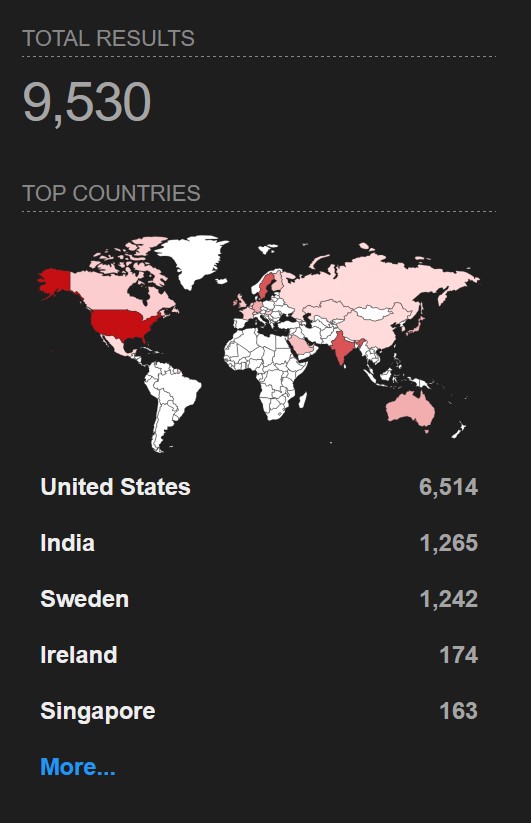
Shodan Dork
http.title:"ServiceNow"ServiceNow CVE-2024-4879 Bulk Scanning
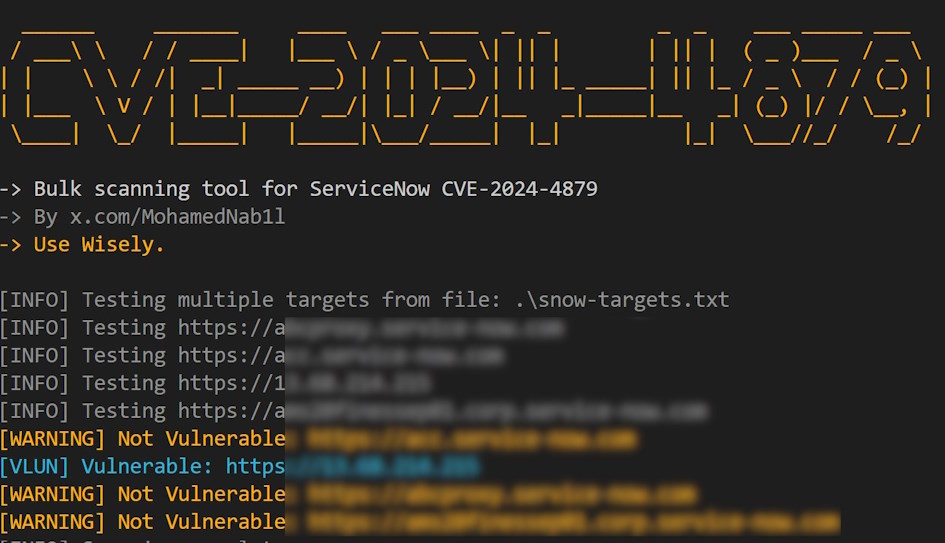
at the time of writing,I couldn’t find any security tool to bulk scan for these new ServiceNow vulnerabilities within my infrastructure, so I wrote a bulk scanning tool that could identify CVE-2024-4879, this tool is an open source tool you may use freely.
How to protect your ServiceNow instances
If you’re a ServiceNow cloud customer, you can breathe a little easier. ServiceNow has already applied the necessary updates to their hosted instances, ensuring that cloud-based customers are protected against these vulnerabilities. However, if you’re running ServiceNow within your own data centers, take immediate action to apply the necessary patches to your on-premises ServiceNow installations.












