Trend Micro has identified an active cryptojacking campaign that exploits exposed Docker remote API servers to deploy cryptocurrency miners. Dubbed “Commando Cat,” this attack campaign has been active since the start of 2024.
The Commando Cat attack gets its name from its initial step: deploying seemingly harmless Docker containers using the Commando project. Commando is an open-source GitHub project that creates Docker images on-demand for developers, making it a trusted resource in the Docker community. By using cmd.cat, a publicly available service, attackers can easily avoid detection and fly under the radar.
The attack begins with an initial access vector, where the attacker deploys a seemingly harmless Docker image named cmd.cat/chattr. Once deployed, the malicious actor creates a Docker container based on this image and uses chroot to break out of the container and gain access to the host operating system. This allows the attacker to peek outside the container and enter the host system using the Binds parameter, which specifies volume bindings.
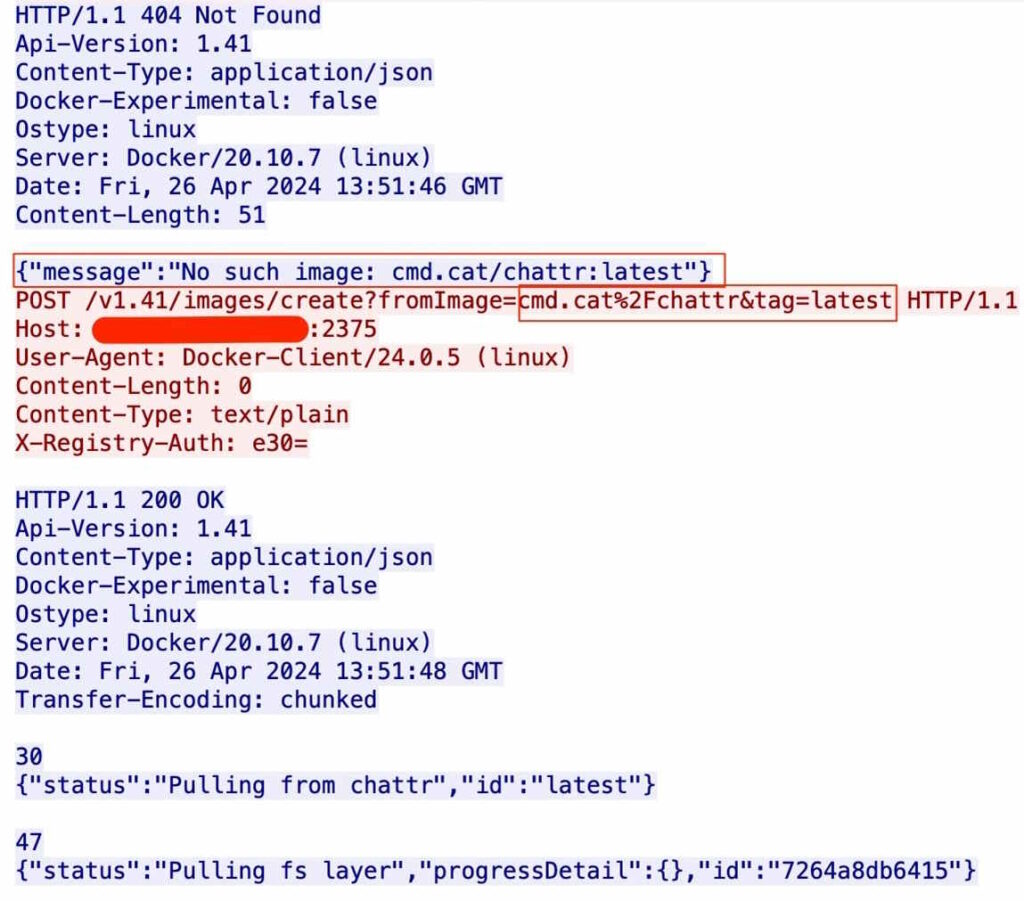
The attacker then uses chroot to bind the host’s root directory into the container’s /hs directory, granting unrestricted access to the host file system.
Once inside the host, the attackers download a malicious binary, potentially an IRC bot called ZiggyStarTux, which is based on the Kaiten malware. This bot, disguised with User-Agent strings like “HackZilla/1.67” or “Mozilla/4.75,” tries to connect to its command-and-control (C&C) server.
By hijacking your server’s resources, the malicious attackers can use your server’s resources to mine digital currencies like Monero, profiting from your resources without your knowledge. This is known as, Cryptojacking.
The Commando Cat attack underscores the critical need for Docker security. Here are some steps you can take:
- Limit API Access: Restrict access to your Docker Remote API. If you don’t need remote access, disable it.
- Use Authentication: Implement strong authentication for any remote access.
- Monitor Containers: Regularly review running containers for any suspicious activity.
- Keep Updated: Ensure your Docker software and images are up-to-date with the latest security patches.