A security researcher, Mykola Grymalyuk, has published details and a proof-of-concept (PoC) code for a macOS vulnerability, CVE-2024-27822, which allows attackers to gain root privileges on macOS devices. This vulnerability affects Apple’s Installer.app and PackageKit.framework, which spawns installation scripts embedded in PKGs (package files) as root within the current user’s environment.
The Vulnerability
The vulnerability lies within Apple’s Installer.app and the PackageKit.framework. These components handle the installation of PKG (package) files, which often contain scripts that run during the installation process. The problem arises when these scripts, particularly those with the #!/bin/zsh shebang, load the user’s .zshenv file while running with root privileges.
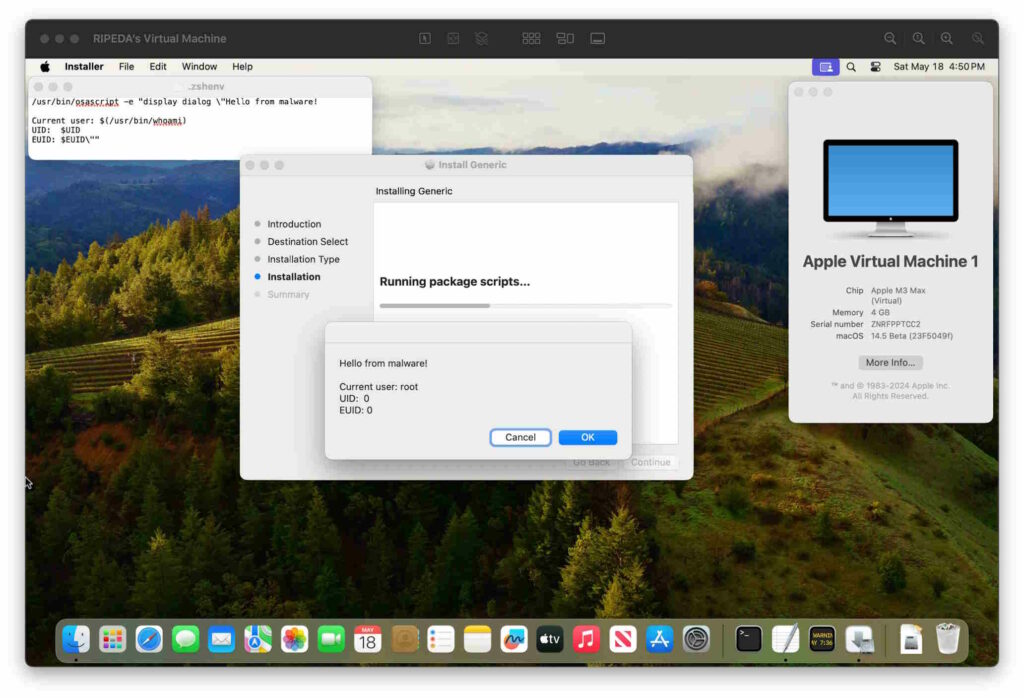
This allows a malicious attacker to insert a malicious payload into the .zshenv file, which is then executed as root user when a ZSH-based PKG is installed by the system user.
The Attack Vector
The primary attack vector for this vulnerability is a logic bomb-based payload. This payload lies hidden within the .zshenv file, waiting for the user to install any ZSH-based PKG. Once the installation begins, the payload is executed, granting the attacker full root access to the system.
Example Payload For CVE-2024-27822:
/usr/bin/osascript -e "display dialog \"Hello from malware!
Current user: $(/usr/bin/whoami)
UID: $UID
EUID: $EUID\""Mykola Grymalyuk has released a POC written in python to demonstrate this attack. The script will create a dummy PKG and inject a payload into the .zshenv file.
Protecting Against the Vulnerability
To protect against this vulnerability, users and administrators should ensure their systems are updated to the latest macOS versions that address this issue:
- Update to macOS 14.5 Beta 2 (23F5059e) or newer
- Update to macOS 13.6.7 (22G720) or newer
- Update to macOS 12.7.5 (21H1222) or newer
Also, macOS users should exercise caution when installing PKGs from untrusted sources and regularly review and secure their local .zshenv files.













