Have I Been Pwned breach notification service, sheds light on a recent and alarming development – the Naz.API Credential Stuffing List. Hunt’s investigation reveals a significant and potentially devastating collection of data that demands attention from the cybersecurity community.
The story begins with a bug bounty submission received by a well-known tech company. The submission was based on a credential stuffing list discovered on a BreachForums. Although the post dates back almost four months, its severity came to the forefront recently, prompting the concerned tech company to take immediate action to protect its substantial user base.
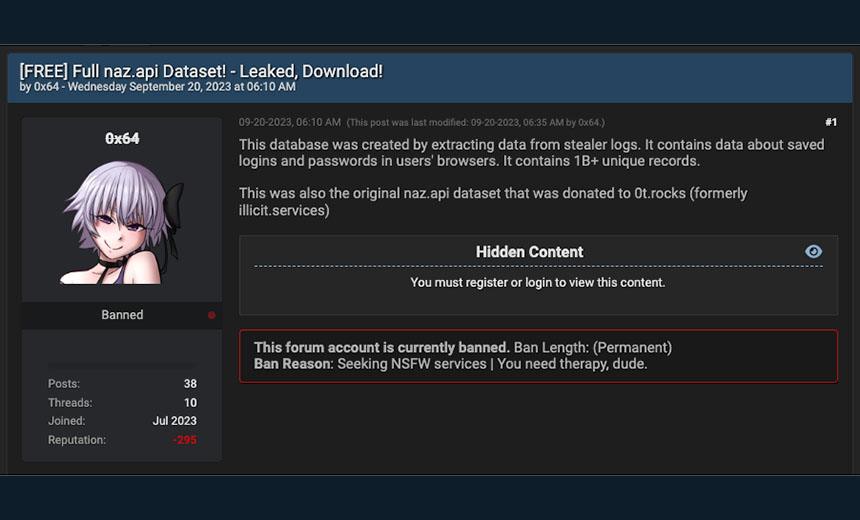
Troy Hunt’s exploration into the Naz.API list unrevealed some interesting statistics that set it apart from the typical credential stuffing incidents. The list comprises a staggering 319 files amounting to 104GB of data, encompassing a jaw-dropping 70,840,771 unique email addresses. Notably, 427,308 individuals who are subscribers to Have I Been Pwned have been directly impacted by this breach.
The most concerning revelation is that 65.03% of the email addresses in the Naz.API list were previously unknown to Have I Been Pwned. This indicates a substantial injection of new data into the cyber threat landscape, far beyond the recycled and repurposed lists commonly encountered. The significance of this discovery is evident – a large portion of the compromised data is fresh and poses a serious threat to user accounts and sensitive information.
As Troy Hunt delves deeper into the origins of this ominous collection, it becomes apparent that the data is sourced from “stealer logs.” These logs, essentially records of credentials stolen by malware from compromised machines, provide a chilling glimpse into the tactics employed by cybercriminals. The Naz.API list is traced back to the now-defunct illicit.services website, infamous for facilitating searches for illicitly acquired data.
The implications of this breach extend far beyond the immediate victims, as the Naz.API list represents a substantial volume of data obtained through malicious means. The urgency for heightened cybersecurity measures is underscored by the fact that a considerable portion of the compromised email addresses were previously unknown, making it imperative for individuals and organizations to be proactive in securing their digital assets.













