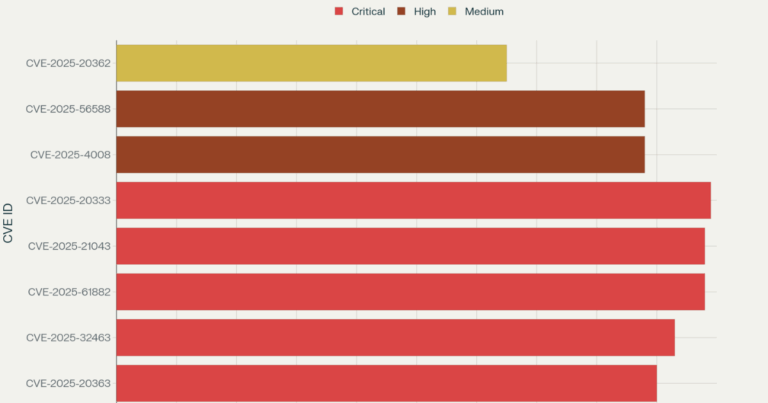
In a recent announcement, Ukraine’s defense intelligence directorate (GUR) has asserted responsibility for a large-scale cyberattack on Russia’s state tax service. According to the GUR statement released on Tuesday, the attack involved infecting thousands of servers belonging to Russia’s federal tax service (FNS) with malware, resulting in the destruction of databases and backups.
The operation reportedly targeted both the central servers in Moscow and more than 2,300 regional servers scattered across Russia and occupied Crimea. The attack also impacted a Russian tech company responsible for operating FNS’s database.
During the cyber assault, GUR claimed to have breached one of the “key well-protected central servers” of the FNS, dealing a severe blow to the agency’s infrastructure. The intelligence directorate asserted that the destruction of configuration files, vital for the functioning of Russia’s tax system, was a significant achievement.
Furthermore, GUR stated that the internet connection between FNS’s central office and its regional branches has been paralyzed, leaving the agency struggling to restore normalcy. The intelligence agency predicted that the FNS might remain “paralyzed” for at least a month and suggested that it might never fully recover from the attack.
While Ukraine’s intelligence claims have been reported, they have not been independently verified. Russian state media has not commented on the alleged cyberattack, and the FNS has not issued a public response.
This is the second cyber operation that GUR has claimed responsibility for targeting a Russian state agency. In November, the intelligence directorate acknowledged its involvement in a successful cyber operation against Russia’s civil aviation agency, Rosaviatsia.
The trend of cyber operations against Russian entities has been escalating, with pro-Ukraine hacker groups and hacktivists previously taking credit for various attacks. In October, a source within Ukraine’s security services (SBU) revealed collaboration with pro-Ukrainian hackers to breach Russia’s largest private bank. Additionally, in November, reports surfaced about the Ukrainian hacker group Blackjack collaborating with the SBU to hack into the website of Russia’s Labor Ministry, allegedly obtaining sensitive military data.
The international community will be closely monitoring the developments surrounding this cyberattack and its potential geopolitical implications. As the situation unfolds, it raises questions about the increasing role of cyber operations in contemporary geopolitical conflicts and the challenges of attributing responsibility in the complex world of cyber warfare.