The popular WPML Multilingual CMS plugin, used by millions of WordPress sites worldwide, allows users to create multilingual content, recently patched a security vulnerability that affects WPML versions 4.6.12 and earlier.
Security researcher Stealthcopter discovered a Remote Code Execution (RCE) vulnerability (CVE-2024-6386) in WPML. This flaw, caused by a Twig Server-Side Template Injection, could allow attackers with contributor-level access permissions or higher to execute malicious code on WPML’s hosted server
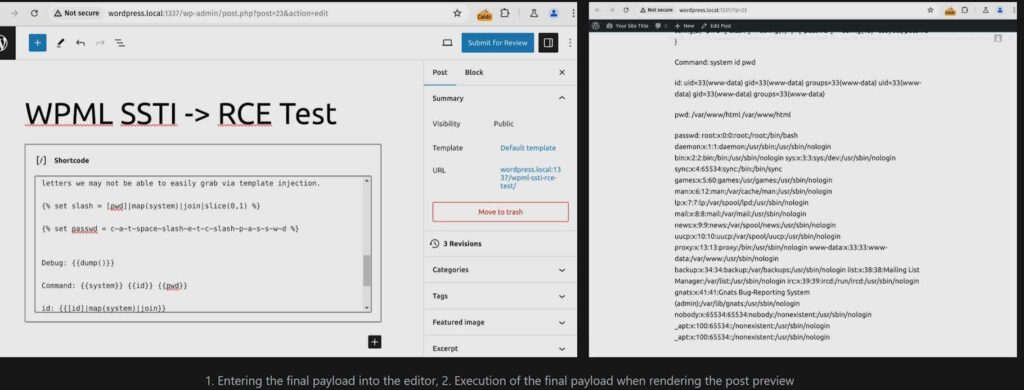
The flaw lies in the callback function within the class-wpml-ls-shortcodes.php file. This function processes shortcode content and passes it to the render function in class-wpml-ls-public-api.php. The shortcode content is passed as the twig_template variable and then rendered as a Twig template string without proper sanitization.
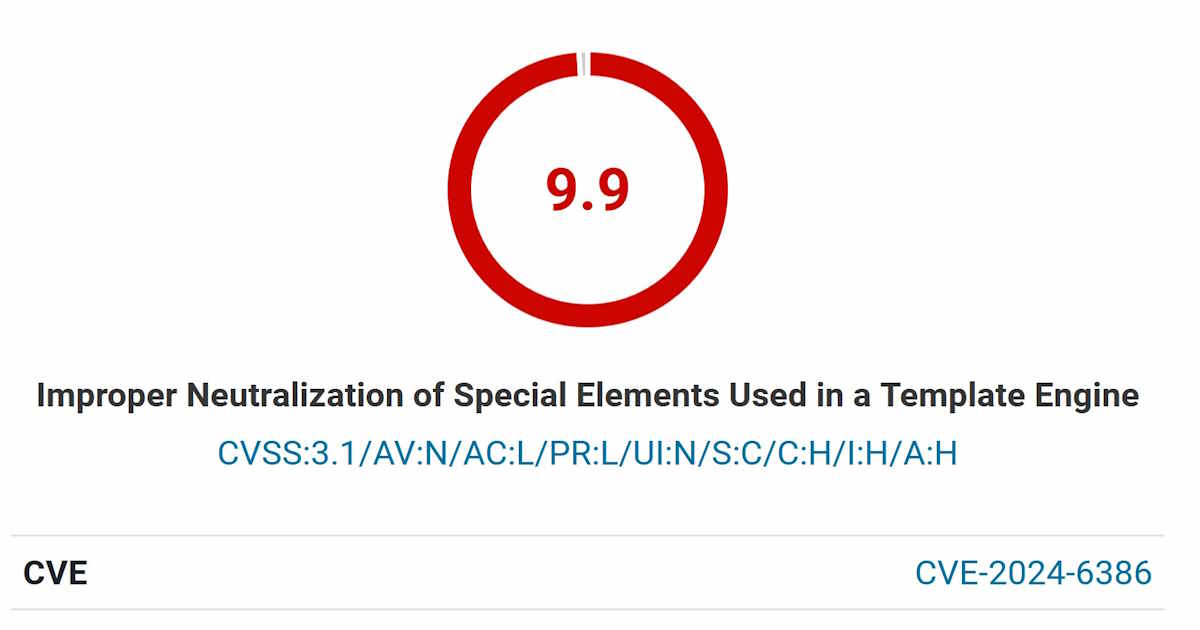
The severity of CVE-2024-6386 vulnerability is high, with a CVSS score of 9.9 (Critical). This means that an attacker could potentially exploit the flaw to execute arbitrary code on the server, leading to data breaches, site defacement, or even full site or server takeover.
The WPML team has already released a patched version of the plugin, 4.6.13, which addresses the vulnerability. To remediate this issue, it’s crucial to update your WPML plugin to the latest version or a newer patched version.